
| Chain INPUT (policy ACCEPT 129 packets, 13250 bytes) pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 49 packets, 5882 bytes) pkts bytes target prot opt in out source destination |

| nmap -sS localhost Starting Nmap 4.20 ( http://insecure.org ) at 2007-03-26 15:20 GMT Interesting ports on localhost: Not shown: 1695 closed ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http MAC Address: 00:00:00:00:00:00 (MSI) Nmap finished: 1 IP address (1 host up) scanned in 1.341 seconds |
| #firwall.sh #!/bin/sh #Effacement de toute les régles de netfilter iptables -F iptables -X #politique par default, tout est interdit. iptables -P INPUT DROP iptables -P OUTPUT DROP iptables -P FORWARD DROP #autorisation loopback iptables -A INPUT -i io -j ACCEPT iptables -A OUTPUT -o io -j ACCEPT #autorisation ICMP pour le ping iptables -A INPUT -p icmp -j ACCEPT iptables -A OUTPUT -p icmp -j ACCEPT #autorisation DNS iptables -A OUTPUT -p udp --dport 53 -j ACCEPT iptables -A INPUT -p udp --sport 53 -j ACCEPT #autorisation pour surfer sur le WEB iptables -A OUTPUT -p tcp --dport 80 -j ACCEPT iptables -A INPUT -p tcp --sport 80 -j ACCEPT |
| Chain INPUT (policy DROP
41 packets, 5161 bytes) pkts bytes target prot opt in out source destination 0 0 ACCEPT all -- io * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 2 242 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp spt:53 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp spt:80 Chain FORWARD (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 ACCEPT all -- * io 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 2 165 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:53 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 |
| Starting Nmap 4.20 ( http://insecure.org ) at 2007-03-27
11:22 GMT All 1697 scanned ports on xxx.xxx.xxx.xxx (xxx.xxx.xxx.xxx) are filtered MAC Address: 00:00:00:00:00:00 (MSI) Nmap finished: 1 IP address (1 host up) scanned in 36.455 seconds |
| nmap -g 80 -sS xxx.xxx.xxx.xxx
Starting Nmap 4.20 ( http://insecure.org ) at 2007-03-27 11:28 GMT Interesting ports on xxx.xxx.xxx.xxx (xxx.xxx.xxx.xxx): Not shown: 1695 closed ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http MAC Address: 00:00:00:00:00:00 (MSI) Nmap finished: 1 IP address (1 host up) scanned in 0.286 seconds |
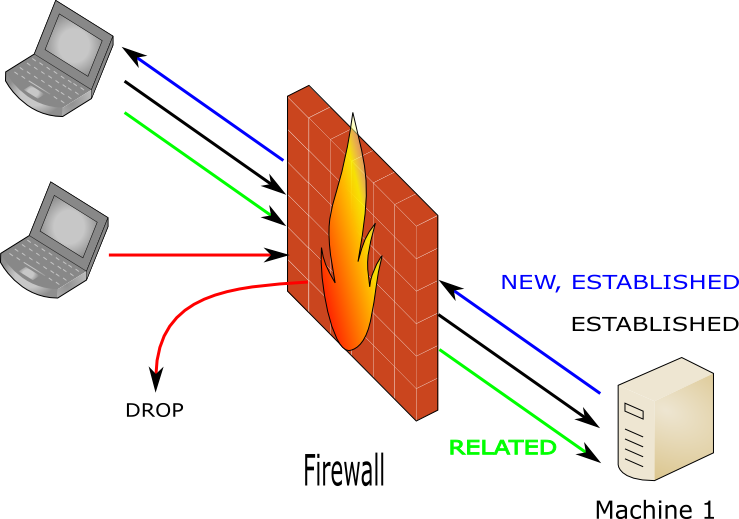
| #!/bin/sh #modules suivi de connexion modprobe ip_conntrack #Sup de la configuration de netfilter iptables -F iptables -X #politique par default, tout est interdit. iptables -P INPUT DROP iptables -P OUTPUT DROP iptables -P FORWARD DROP #autorisation loopback iptables -A INPUT -i io -j ACCEPT iptables -A OUTPUT -o io -j ACCEPT #autorisation ICMP iptables -A INPUT -p icmp -m state --state ESTABLISHED -j ACCEPT iptables -A OUTPUT -p icmp -j ACCEPT #autorisation Sortantes TCP LAN->WAN iptables -A OUTPUT -p tcp -m multiport --dports 80 -m state --state NEW,ESTABLISHED -j ACCEPT #autorisation Reponses TCP WAN->LAN iptables -A INPUT -p tcp -m multiport --sports 80 -m state --state ESTABLISHED -j ACCEPT #autorisation Sortantes UDP LAN->WAN iptables -A OUTPUT -p udp -m multiport --dports 53 -m state --state NEW,ESTABLISHED -j ACCEPT #autorisation Reponses UDP WAN->LAN iptables -A INPUT -p udp -m multiport --sports 53 -m state --state ESTABLISHED -j ACCEPT |
| Chain INPUT (policy DROP 37 packets, 7390 bytes) pkts bytes target prot opt in out source destination 0 0 ACCEPT all -- io * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 state ESTABLISHED 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 multiport sports 80 state ESTABLISHED 2 242 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 multiport sports 53 state ESTABLISHED Chain FORWARD (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy DROP 8 packets, 836 bytes) pkts bytes target prot opt in out source destination 0 0 ACCEPT all -- * io 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 multiport dports 80 state NEW,ESTABLISHED 2 165 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 multiport dports 53 state NEW,ESTABLISHED |
| nmap -g 80 -sS xxx.xxx.xxx.xxx
Starting Nmap 4.20 ( http://insecure.org ) at 2007-04-12 10:24 GMT All 1697 scanned ports on xxx.xxx.xxx.xxx (xxx.xxx.xxx.xxx): are filtered MAC Address: 00:00:00:00:00:00 (MSI) Nmap finished: 1 IP address (1 host up) scanned in 36.452 seconds |
| cat knockd ################################################ # # knockd's default file, for generic sys config # ################################################ # control if we start knockd at init or not # 1 = start # anything else = don't start START_KNOCKD=1 # command line options KNOCKD_OPTS="-i eth0" |
| [options] logfile = /var/log/knockd.log [openSSH] sequence = 7000,8000,9000 seq_timeout = 5 command = /sbin/iptables -A INPUT -s %IP% -p tcp --dport 22 -j ACCEPT && /sbin/iptables -A OUTPUT -m state --state NEW,ESTABLISHED -j ACCEPT tcpflags = syn [closeSSH] sequence = 9000,8000,7000 seq_timeout = 5 command = /sbin/iptables -D INPUT -s %IP% -p tcp --dport 22 -j ACCEPT && /sbin/iptables -D OUTPUT -m state --state NEW,ESTABLISHED -j ACCEPT tcpflags = syn |
| Starting Nmap 4.20 ( http://insecure.org ) at 2007-04-12
11:19 Romance Daylight Time Interesting ports on xxx.xxx.xxx.xxx (xxx.xxx.xxx.xxx): PORT STATE SERVICE 22/tcp open ssh 80/tcp filtered http MAC Address: 00:00:00:00:00:00 (MSI) Nmap finished: 1 IP address (1 host up) scanned in 1.526 seconds |
| Starting Nmap 4.20 ( http://insecure.org ) at 2007-04-12
11:24 GMT Interesting ports on xxx.xxx.xxx.xxx (xxx.xxx.xxx.xxx): PORT STATE SERVICE 22/tcp filtered ssh 80/tcp filtered http MAC Address: 00:00:00:00:00:00 (MSI) Nmap finished: 1 IP address (1 host up) scanned in 1.406 seconds |